Why ad block circumvention failed as a monetization strategy
The perpetual tug of war between publishers seeking more revenue and users seeking a cleaner browsing experience led to the meteoric rise in adoption of ad blocking tools. At last count, 820M devices were blocking ads globally.
As a natural consequence of this increase in adoption, publishers began to lose a part of their audience, and the revenue that goes along with that audience.
This is the context from which ad block circumvention emerged, providing a technological hide-and-seek, where publishers (or technology vendors) utilize various strategies to bypass ad blockers and sneak ads into user sessions.
While initial models of circumvention sought to reclaim dwindling advertising revenues, the lifecycle of this approach has been mired by a lack of respect for user choice, ethical considerations, and a never-ending pursuit of technical loopholes.
In this article on circumvention, we unpack its methods, evaluate its ethical and practical implications, as well as its effectiveness and shortcomings as a strategy.
What is ad block circumvention
Ad block circumvention is a tactic employed by some technology vendors and publishers to detect the presence of ad blockers within a user’s session and render them non-functional by exploiting technical loopholes or other measures.
It is also sometimes called “ad re-insertion”, which hints that the ad is being forcibly re-inserted despite the presence of an ad-blocker.
Ad re-insertion was one of the earliest attempts to get around ad blockers, in a bid to protect and recoup the advertising revenue that was being lost due to the growing user adoption of ad blocking tools.
Over time, better and more respectful approaches to monetization have been established to achieve the same goal, and ongoing efforts to circumvent ad blockers today exist only in small pockets of the industry.
(Fun fact: As one of the earliest companies in this space, Blockthrough also started its journey with ad re-insertion, before pivoting to programmatic monetization via Acceptable Ads.)
How ad block circumvention works
Broadly speaking, circumvention can be broken down into three main categories.
Cloaking
With cloaking, publishers try to route ads through channels that ad-blockers do not have visibility into due to bugs or technical limitations.
For instance, attempts have been made to detect the presence of an ad-blocker, and in response, open up a WebSocket connection as a backup channel for delivering ads. More recently, DNS CNAME values have been manipulated to disguise HTTP requests made to advertising and tracking domains as first-party requests.
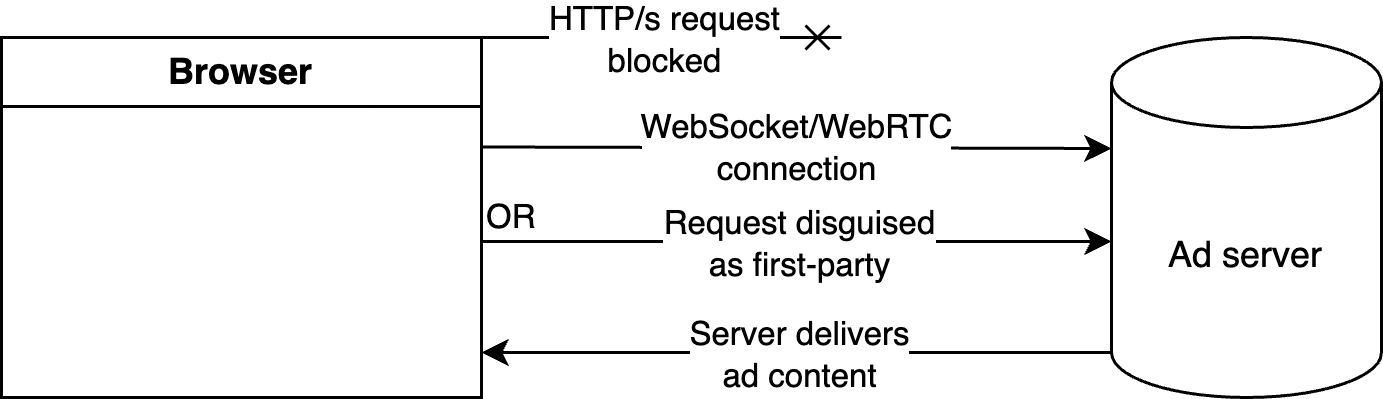
Cloaking attempts don’t have a long shelf life because the exploits that are used to implement them are usually patched by platforms or extension developers in due course of time.
The WebSocket exploit, for instance, was neutralized once Chrome patched the WebRequest API to allow developers to intercept related network requests. In addition, Cloaking techniques are ineffective against ad-blocking methods that don’t rely on the extensions API.
Obfuscation
In this category of circumvention, publishers attempt to evade filter list rules by obfuscating the naming of web content—domain, URL path, element ID, etc.—which are related to ad requests.
Compared to cloaking techniques, obfuscation can be more powerful because it targets inherent weaknesses in how filter lists work: Filter lists have to be precise enough to avoid false positives and inadvertently block elements that are not ads, at the same time, updating filter lists is a manual and time-consuming process.
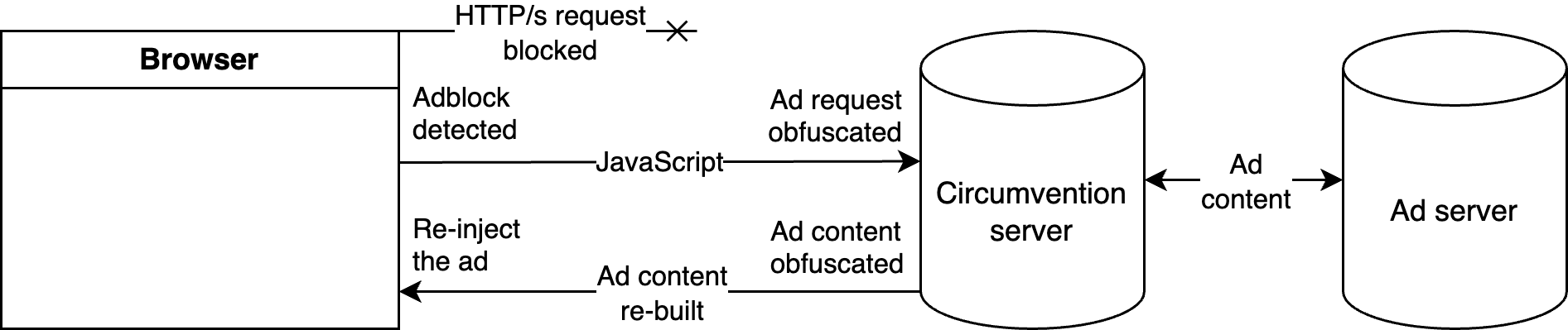
(If you’re wondering what filter lists are, think of them as a list of signatures. An ad-blocker that uses filter lists matches the contents of the web page and network requests against those in the filter list—if a match is found—the request is aborted. Now, back to the guide.)
For instance, the most widely used ad blocking filter list, known as EasyList, is still manually maintained by the enthusiasts who created it and the volunteers who support it.
Obfuscation is a sophisticated response to ad blocking, wherein a server sits between the web page and the third-party ad server, and manages the ad delivery lifecycle, including obfuscating requests from and to the webpage, de-obfuscating and relaying requests to and from the ad server, and finally re-building the ad content and re-inserting it on the web page.
Other methods
Although the era of peak circumvention is all but over, as long as there are ad blockers, there will be parties that will want to get around them.
The defining characteristic of circumvention does not lie in its technical implementation, but the intent to disregard user choice and experience. Here are some other methods that have been used as a means to circumvent:
- Server-side ad insertion (SSAI): For pre-roll or mid-roll video ads, advertising content can be stitched directly into the primary content on the server-side, and the resulting video is delivered as a single stream to the end user. Since no network requests for ad serving are initiated, there is nothing for ad-blockers to detect and intercept.
- Native advertising: Native ad units and their elements can be named and styled to match the primary content on the web page, making it somewhat harder for ad-blockers to distinguish between advertising and content. Without clear and proper labeling for users, such ads can also be misleading in some cases.
- Domain rotation: Technically a subset of cloaking, by continuously switching the domains that host ad serving resources, vendors and publishers can temporarily get around ad-blockers, until a new rule is added to the filter list. The domains are usually a combination of gibberish words, inexpensive, and easily discarded.
- Fingerprinting: Fingerprinting is an attempt to identify a user by building a unique signature that includes a combination of signals, including IP address, geo, unique device IDs, etc. While fingerprinting is not used to circumvent ad-blockers, it can be used to circumvent tracking prevention, such as Safari’s ITP, or privacy-focused extensions.
- Fallback creatives/messages: By detecting that third-party ad requests are being blocked, publishers can collapse the ad container and replace it with a fallback creative that is named and styled to resemble page content. It can then be used to serve a notice to adblock users, in-house ads, or direct (non-programmatic) campaigns.
- Yet other methods of circumvention include the use of proxy servers, script mutation, dynamic element naming, and other forms of non-standard ad delivery.
Why ad block circumvention has failed
Decidedly anti-user approach
Circumvention attempts to force an advertising experience on users against their choice. The blatant disregard of what the users want is the most crucial reason why circumvention fell out of favor with most reputable publishers and failed as a strategy over time. Actively choosing an anti-user approach can have a range of short-term and long-term consequences, such as users existing the website in frustration or developing a poor opinion of the publisher’s brand.
Doesn’t fix the underlying problem
Users who block or filter advertising on the web do it for a variety of well-studied reasons, chief among them being the desire to avoid annoying or interruptive experiences, speed up browsing, protect themselves against security risks, conserve battery and network bandwidth, etc. Circumvention attempts operate on the assumption that these are not genuine concerns and therefore focus on attacking the symptom rather than addressing the underlying problem.
Whac-A-Mole business model
Circumvention is a classic case of Prisoner’s Dilemma, a thought experiment in game theory that describes a situation where two players acting selfishly results in a suboptimal choice for both. Any novel attempt to circumvent ad-blockers may work for a limited period of time, until the affected platforms and extension developers identify and address the vulnerability and move on to the next. In this case, the party attempting to circumvent becomes the Mole that is whac’d.
Poor page and revenue performance
As explained previously in the section on obfuscation-based circumvention, the implementation process of bypassing ad-blockers can get quite convoluted, which means heavier code on the publishers’ web page, more processing time, and higher rates of failed renders—ultimately degrading page performance for users. Combined with the fact that ad serving outages are common, the revenue performance from circumvention-based solutions tends to be unreliable.
Extensions keep getting smarter
Developers don’t sit idly by when someone attempts to degrade the experience of millions of users. In the early years, circumvention attempts were quashed by the volunteers that freely devoted their time to expand the filter lists by adding new rules. More recently, a lot of academic research has been produced on the subject, and extension developers have implemented machine learning models to automate the detection and blocking of circumvention signatures.
Signs you’re being pitched circumvention
Most forward-thinking publishers moved away from circumvention tactics a long time ago, as a newer breed of solutions emerged that were more respectful of user choice and tried to balance that against the need for publishers to grow revenue and stay profitable.
As noted in this Adweek exclusive, “They [circumvention vendors] all failed for the same reason,” says Paul Bannister, Chief Strategy Officer of Raptive (formerly CafeMedia) about their early experiments working with vendors to recover ad-blocked revenue. “That would work for a week, then the ad blockers would figure out the masking and block it. But ultimately we were doing something that was really against the wishes of the user.”
A lot of people in the industry have had to learn the hard lesson that circumvention doesn’t deliver on its promise, however, new companies still pop up every now and then—trying to sell old wine in a new bottle.
Here are some telltale signs that you’re being sold circumvention:
- The vendor has a hard time clearly explaining how their technology works
- The vendor does not comply with any industry ad quality standards, such as Acceptable Ads Standard or Better Ads Standard, or affiliate with any reputable trade associations
- The vendor makes claims that sound too good to be true, for instance, promising to recover 90% of 100% of the revenue that you’re losing due to ad-blockers
- The vendor is unable to share any social proof or testimonials
- The vendor claims that they can recover all types and formats of advertising
We recommend publishers to be thorough in their due diligence with new vendors. Make sure you have a good understanding of how the technology works, that the vendor is able to connect you to other customers who can vouch for the solution’s legitimacy and effectiveness, and that the technology is not subjecting your users to an experience that you wouldn’t on your own.